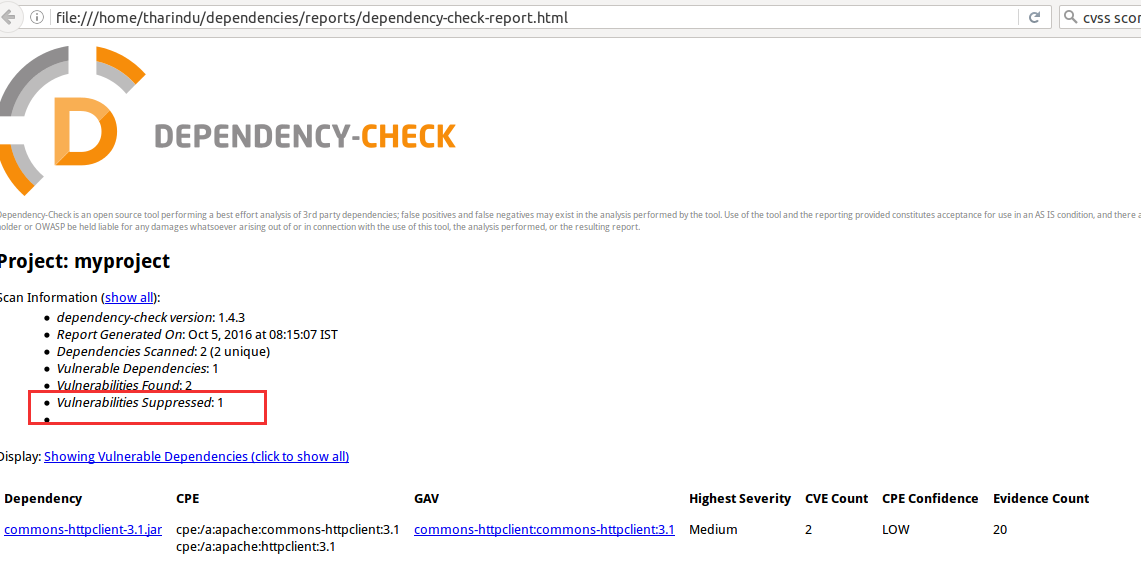
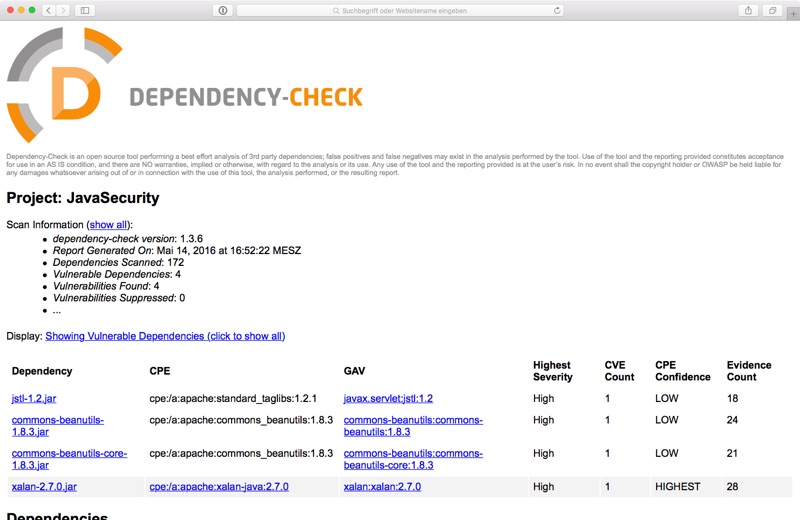
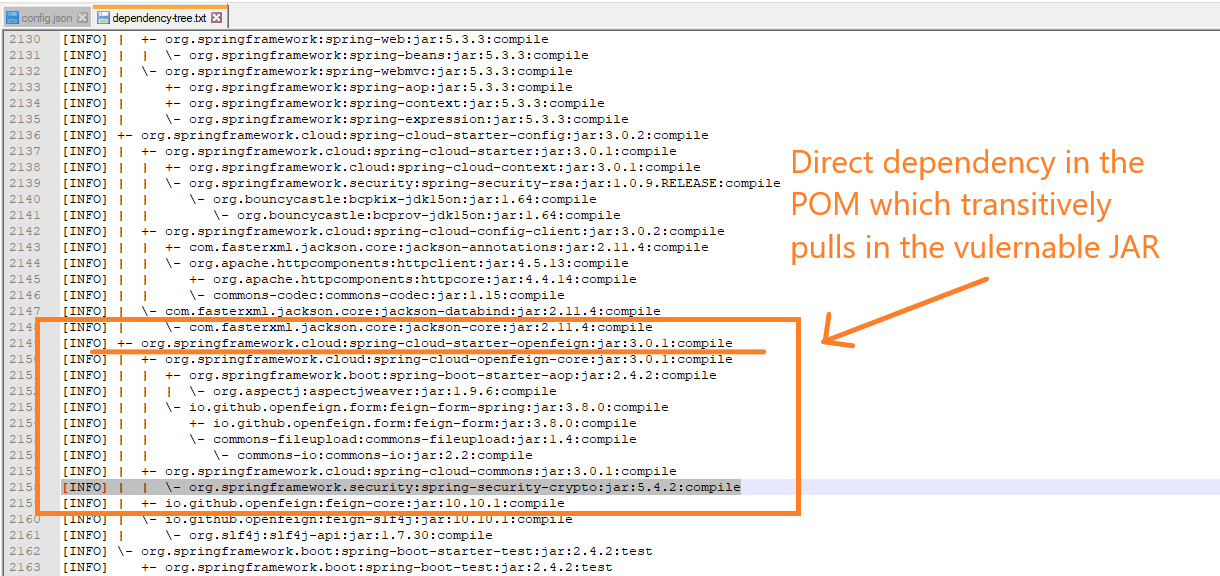
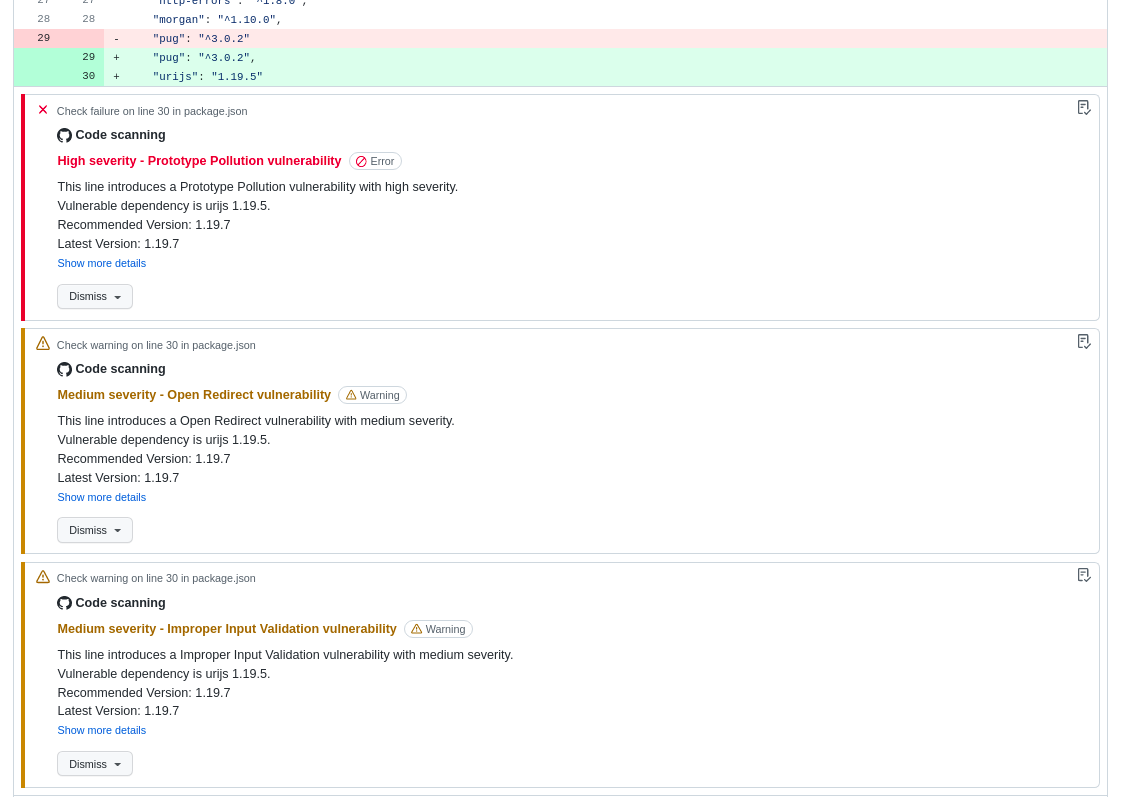
GitHub - Afrouper/MavenDependencyCVE-Scanner: A simple and fast Maven dependency vulnerability scanner. Check existence of vuln JARs (transitive)
GitHub - Xh4H/Loki: The Dependency Confusion vulnerability scanner and autoexploitation tool to help identifying and mitigating supply chain attacks

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog